A new Ransomware as a Service, or RaaS, called Ransom32 has been discovered that for the first time uses a ransomware written in Javascript. Located on an underground TOR site, the Ransom32 RaaS is a simple, but efficient, service where anyone can download and distribute their very own copy of the ransomware executable as long as they have a bitcoin address. For offering this service, the developers of Ransom32 take a 25% cut of all ransom payments and then forward the rest to the bitcoin address an affiliate entered when they joined the affiliate program. Another article with great analysis of the Ransom32 infection was written by Fabian Wosar and posted on the Emsisoft blog.
The Ransom32 Affiliate System
Ransom32 was first reported by infected users in our forums and when Fabian Wosar of Emsisoft and Security Researcher xXToffeeXx searched for a sample they stumbled upon the Ransom32 TOR affiliate service. It is very easy for an affiliate to join this RaaS as all that is needed is a bitcoin address that the affiliate's share of the ransom payment will be sent to.
Once a bitcoin address is submitted, an affiliate will be shown an Affiliate Console where they can see the statistics for their personal distribution campaign and configure various settings on how the ransomware should be executed.
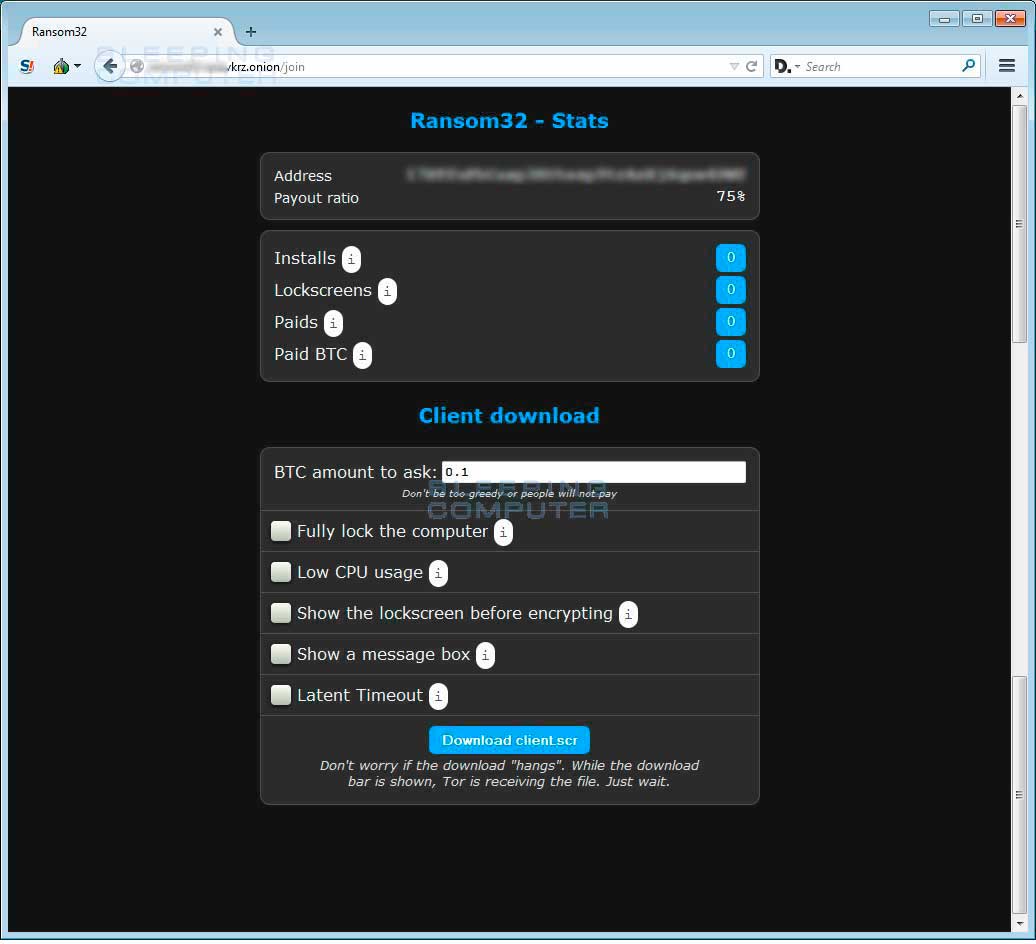
This affiliate console will contain statistics that include the number of people that successfully installed the client, the number of people that were shown the lock screen when the encryption was completed, the number of bitcoin transactions to your address, and the amount of ransom payments sent to your payout address.
In the console an affiliate will also be able to configure various settings for how the Ransom32 executable should run. The listed settings and the Ransom32 developer's descriptions for them are:
BTC amount to ask: BTC amount to ask. Don't be too greedy or people will not pay
Fully lock the computer: By default the lockscreen will popup each X seconds after being minimized. You can configure it so the user will not be able to minimize the lock screen. The downside is that will be more difficult for the users to check that their files were truly encrypted and also they will need to find another method to send your Bitcoins as the browser will be blocked too
Low CPU Usage: Will encrypt files at 0-25% speed while the lock window is not shown, so the process won't be noticeable in the task manager by an advanced user because of high CPU consumption
Show the lockscreen before encrypting: By default the client will show the lockscreen after encrypting part of the files in the computer (filesize under 50 Mb) and continue encrypting in the background. You can tell it to show the lockscreen right after installing, before encrypting any file in the background. The downside is that if the user tries to check his files just when the window pops in, he will notice that any file has been encrypted (although it is encrypting while is running)
Show a message Box: This box will be shown before installing and before any latent timeout is applied.
Latent Timeout: The client will "wake up", connect to the server and start encrypting after this amount of seconds passed after installing. The client won't connect to the server until it wakes up (more stealth), so you won't notice an install in your stats until this moment. NOTE: The client will not save the latent info as-is. Will be mixed with some data so is not understandable at first sight. Because of this, expect a 0-4 minutes drift to your timeout.
Once an affiliate has configured the ransomware to their liking, they simply need to click on the download button to generate and download their customized copy of Ransom32. This download is a self-extracting RAR file that weighs in at 22MB and when extracted totals over 67MB. Once the customized ransomware is downloaded, it is up to the affiliate to determine how it should be distributed.
An important feature for any "commerce" campaign is to be able to track its performance. As only a bitcoin address is required to join the affiliate program, it is very easy for an affiliate to track each distribution method's performance by simply using a different address for each campaign.
The Ransom32 Ransomware Encryption Process
The download that is generated by the affiliate is actually a 22MB self-extracting archive that when extracted is over 67MB. When this executable is run, it will extract numerous files into the C:\Users\User\AppData\Roaming\Chrome Browser folder and creates a shortcut in the Start Menu's Startup Folder called ChromeService so that the ransomware starts at login. The shortcut points to a chrome.exe executable that is actually a NW.js package that contains Javascript code that will encrypt the victim's data and then display a ransom note.
The files extracted into the Chome Browser folder are:
- chrome - The Chromium license agreement.
- chrome.exe - This is the main executable for the malware and is a packaged NW.js application bundled with Chromium.
- ffmpegsumo.dll - HTML5 video decoder DLL that is bundled with Chromium.
- g - The settings file that contains various information used by the malware. This information includes the affiliate's ransom amount, bitcoin address that they receive payments on, and error message that is shown in a messagebox if the Show a message Box setting was enabled.
- icudtl.dat - File used by Chromium
- locales - Folder containing various language packs used by Chrome.
- msgbox.vbs - The messagebox displayed if the affiliate enabled the Show a message Box setting.
- nw.pak - Required for the NW.JS platform.
- rundll32.exe - Renamed TOR executable so that the malware can communicate with the TOR Command and Control server.
- s.exe - Renamed Shortcut.exe from OptimumX. This is a legitimate program used by the malware to create the ChromeService shortcut in the Startup folder.
- u.vbs - A VBS script that deletes a specified folder and its contents.
When encrypting your data, Ransom32 will target only specific file extensions and encrypt them using AES encryption. The targeted file extensions are:
.jpg ,.jpeg ,.raw ,.tif ,.gif ,.png ,.bmp ,.3dm ,.max ,.accdb ,.db ,.dbf ,.mdb ,.pdb ,.sql ,.*sav* ,.*spv* ,.*grle* ,.*mlx* ,.*sv5* ,.*game* ,.*slot* ,.dwg ,.dxf ,.c ,.cpp ,.cs ,.h ,.php ,.asp ,.rb ,.java ,.jar ,.class ,.aaf ,.aep ,.aepx ,.plb ,.prel ,.prproj ,.aet ,.ppj ,.psd ,.indd ,.indl ,.indt ,.indb ,.inx ,.idml ,.pmd ,.xqx ,.xqx ,.ai ,.eps ,.ps ,.svg ,.swf ,.fla ,.as3 ,.as ,.txt ,.doc ,.dot ,.docx ,.docm ,.dotx ,.dotm ,.docb ,.rtf ,.wpd ,.wps ,.msg ,.pdf ,.xls ,.xlt ,.xlm ,.xlsx ,.xlsm ,.xltx ,.xltm ,.xlsb ,.xla ,.xlam ,.xll ,.xlw ,.ppt ,.pot ,.pps ,.pptx ,.pptm ,.potx ,.potm ,.ppam ,.ppsx ,.ppsm ,.sldx ,.sldm ,.wav ,.mp3 ,.aif ,.iff ,.m3u ,.m4u ,.mid ,.mpa ,.wma ,.ra ,.avi ,.mov ,.mp4 ,.3gp ,.mpeg ,.3g2 ,.asf ,.asx ,.flv ,.mpg ,.wmv ,.vob ,.m3u8 ,.csv ,.efx ,.sdf ,.vcf ,.xml ,.ses ,.dat
Notice how Ransom32 also uses wild cards in the targeted file extensions. This allows the program to to target a greater variety of extensions. For example, with the .*sav* extension, not only will .sav files be targeted, but also files ending with .save, .gamesave, or .mysaves will be encrypted as well. When encrypting data files, it does not rename a victim's files and will not encrypt any files located in the following folders:
windows
winnt
programdata
boot
temp
tmp
$recycle.bin
When it has finished encrypting your data it will display the Ransom32 ransom lock screen/ransom note as shown below.
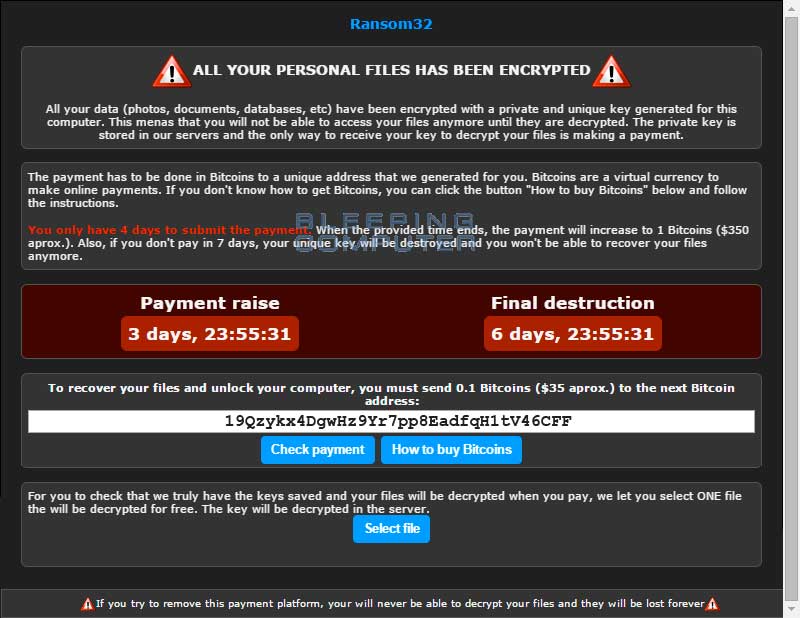
The Ransom32 lock screen will display information that tells the victim what has happened to their files, how to pay the ransom, the ransom amount, and the bitcoin address a ransom payment is sent to. The language used by the lock screen is shown in either English or Spanish, with the default appearing to be English. Last, but not least, this screen allows you to decrypt one file for free to prove that it can be done.
Unfortunately, at this time there is no known way to decrypt the files for free, but if anything changes we will be sure to post about it here. For a more thorough and detailed explanation on how the Ransom32 utilizes NW.js and encrypts your data, please see this Emsisoft article.
The first Javascript Ransomware
What makes this ransomware unique is that it is the first ransomware programmed entirely in Javascript, HTML, and CSS. This ransomware uses the NW.js platform that allows developers to create native applications for Linux, Mac, and Windows using HTML5, CSS3, Javascript, and WebGL. Using NW.js a developer can take their scripts and html and package them into a Chromium executable that when executed automatically runs the embedded JS and HTML.
What makes the Ransom32 RaaS so scary is that Javscript and HTML are cross-platform and run equally as well on Macs and Linux as they do in Windows. This means that with some minor tweaks, the Ransom32 developers could easily make NW.js packages for Linux and Mac computer. Though there does not seem to be any indication that this is being done as of yet, doing so would be trivial.
It is inevitable that ransomware will be created for operating systems other than Windows. Using a platform like NW.js just brings us one steps closer.
Files installed by Ransom32:
%Temp%\nw3932_17475
%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\ChromeService.lnk
%AppData%\Chrome Browser\
%AppData%\Chrome Browser\.chrome\
%AppData%\Chrome Browser\.chrome\cached-certs
%AppData%\Chrome Browser\.chrome\cached-microdesc-consensus
%AppData%\Chrome Browser\.chrome\cached-microdescs
%AppData%\Chrome Browser\.chrome\cached-microdescs.new
%AppData%\Chrome Browser\.chrome\lock
%AppData%\Chrome Browser\.chrome\state
%AppData%\Chrome Browser\chrome
%AppData%\Chrome Browser\chrome.exe
%AppData%\Chrome Browser\ffmpegsumo.dll
%AppData%\Chrome Browser\g
%AppData%\Chrome Browser\icudtl.dat
%AppData%\Chrome Browser\locales\
%AppData%\Chrome Browser\msgbox.vbs
%AppData%\Chrome Browser\n.l
%AppData%\Chrome Browser\n.q
%AppData%\Chrome Browser\nw.pak
%AppData%\Chrome Browser\rundll32.exe
%AppData%\Chrome Browser\s.exe
%AppData%\Chrome Browser\u.vbs


Comments
Intimacygel - 8 years ago
Can you give us the onion link for the generator?
ericperrot - 8 years ago
I found an archive for the server :
http://www.mediafire.com/download/fy97r72azwtdhyc/ransom32server.scr
NickAu - 8 years ago
Members are advised not to download this software.
Hunting.Targ - 8 years ago
I have learned less scary and costly lessons about backup. The best backup strategy IMO is to have an external drive that is physically connected for backup and disconnected after backup is complete. I don't remember where I got this quote from, but "If it has an IP stack, it will be attacked." Physical disconnection of a backup storage medium is a failsafe against anything that gains read/write access to a system's file structure.
awesomecooldude101 - 8 years ago
welp....this is great, now script kiddies can make damaging ransomeware viruses and distribute them to unwary users...